.jpg?width=820&height=547&name=_2024%20-%20Blog%20Website%20Redesign%20Featured%20Images%20(8).jpg)
Ingestion Methods and Attack Surface
Modern organizations that leverage the cloud ingest data into storage from various sources. Some examples include:
- Customer data via web applications
- On-premises data via migration tools such as AWS DataSync
- Data transferred from partners utilizing managed file transfer (MFT) services like AWS Transfer Family
- Data gathered from mergers and acquisitions
- Data scraped from the public internet
When you ingest data from one or many untrusted sources, there is no way to guarantee that your data is free from threats, including malware. Additionally, much of this data can be sensitive and regulated by compliance frameworks. This information is often vital to the operation of your business. If your organization uses Amazon storage services like Amazon S3 or Amazon EFS, it is your responsibility to secure that data by ensuring that some form of malware protection is enabled.
Malware Protection for Amazon S3
One of the simplest and most popular solutions on the market is Amazon GuardDuty Malware Protection for S3. Made generally available in June of 2024, GuardDuty Malware Protection for S3 is an easy-to-configure solution that scans data at the object level. You can scan all data in a bucket or limit scanning to specific object prefixes so that GuardDuty only scans uploaded objects that start with one of the selected prefixes.
Event-based scanning checks new objects for malware using a single engine and Amazon intelligence. When an object gets uploaded to the selected bucket or one of the prefixes, GuardDuty downloads that object from the S3 bucket into an isolated environment in the same Region to read it, decrypt it, and scan it. You can quarantine files by setting up tagging and Lambda management. GuardDuty will scan files up to 5 GB across 25 buckets per region per account (see Quotas in Malware Protection for S3).
Extending Protection
GuardDuty Malware Protection for S3 validates the security of data contained within Amazon S3 buckets. However, there are a number of factors to consider when attempting to validate the security of all data within AWS storage.
- You Need Protection Beyond Amazon S3: If data is written to or pushed into Amazon EBS, Amazon EFS or Amazon FSx, it also requires protection. AWS offers GuardDuty Malware Protection for EC2, which helps detect the potential presence of malware by scanning the Amazon Elastic Block Store (Amazon EBS) volumes that are attached to Amazon Elastic Compute Cloud (Amazon EC2) instances and container workloads running on Amazon EC2. However, GuardDuty doesn't support Amazon EFS or Amazon FSx.
- You Need to Scan Pre-Existing Objects: Objects already residing in S3 should also be scanned-and rescanned-for malware.
- You Need Support for More Buckets and Larger Files: You may have files larger than 5GB or more than 25 buckets per region per account that need protection.
- You Need GovCloud Support: GuardDuty Malware Protection for S3 is currently a commercial-only solution, it is not supported in either AWS GovCloud (US) Region.
Cloud Storage Security (CSS) provides malware protection functionality that complements and extends GuardDuty Malware Protection for S3. When Amazon GuardDuty is used in conjunction with an industry-leading antimalware tool like Cloud Storage Security's Antivirus for Amazon S3, you can ensure comprehensive antivirus coverage, and be assured that your entire cloud storage environment is secure. CSS’s malware protection solution allows you to:
- Scan files and volumes across all AWS storage services including S3, EBS, EFS, FSx.
- Manage malware detected by Amazon GuardDuty via automated quarantine as well as detonation capabilities.
- Augment or replace the engines utilized by Amazon GuardDuty by utilizing CSS's combined power of multiple industry-leading malware detection engines.
- Utilize a simple console that enables the management of large and complex configurations, quick analysis of results, and the ability to scale malware protection to thousands of buckets and hundreds of AWS accounts.
- Scan and protect not just new objects, but also existing files on an on-demand or scheduled basis, as well as before files are written to storage utilizing an API scanning model.
- Scan files greater than 5GB in size.
- Scan data in GovCloud regions.
The additional functionality CSS offers is useful to organizations looking to extend malware protection coverage across more of their data.
Quarantining Functionality
CSS provides customers with the ability to configure file handling directly inside the console without writing Lambda functions. By navigating to the Scan Settings page in the CSS console, users can choose a file handling policy (keep, delete, quarantine), select a quarantine bucket, if desired, and if configured, have all files discovered to contain malware be sent directly to that bucket upon reception of the verdict.
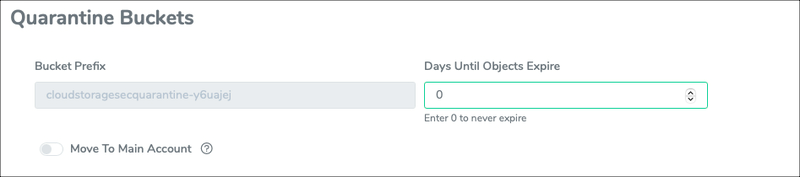
Figure 1. Quarantine options within CSS console.
To set up quarantining in your CSS console, select “Quarantine” in the File Handling Policy pane, decide whether or not objects should be moved cross-account to the main account, enter in the prefix for the quarantine bucket and choose a number of days before objects expire.
After a file is quarantined you have the option to perform a static and dynamic analysis to see what the reputation of the file is and understand what it’s attempting to execute. You can also use the Intelligent Analysis integration to retrieve more information on the identities our scanning engines have found along with any available remediation information for cleansing the file of any infection or removing the infection from the end-users machine.
If the above analysis doesn’t yield enough information to make a decision on whether the file is legitimately infected you can then download the file and analyze its code further using tools such as IDA Pro or Ghidra.
If you determine that a file is safe to be allowed back into your production bucket, you can choose to “allow once” so the next time the same file is scanned it will be flagged as infected once again. Alternatively, if you are confident the file is truly clean and the infected finding is a false positive then you can allow the file through permanently so if it’s scanned in the future it will be found as “clean.”
Malware Detonation Functionality
To further investigate suspicious or infected files, CSS offers customers:
- Static Analysis: Send the file to an outside cloud sandbox for analysis
- Dynamic Analysis: Send the file to an outside cloud sandbox for detonation and resulting analysis
Running a static analysis on an infected file will send the hash of the file and the file itself to the cloud sandbox and return information on its reputation, leveraging vast data repositories (including information collected from CSS partner networks, endpoint and mobile telemetry, malware samples, threat campaigns, spam traps, honeypots, open source and proprietary industry intel sharing, web crawlers, and domain reputation databases), along with a VirusTotal report which allows you to see how other scanning engines view and treat the finding.
By using dynamic analysis (malware detonation), CSS customers can view exactly what actions that suspicious or infected file would perform if executed in a downstream environment.
To run dynamic analysis (malware detonation) on a discovered file, navigate to the Findings page on the left hand side of the CSS console, choose which file you’d like to detonate, click the three dots (...) on the final column, and select “Run Dynamic Analysis”.
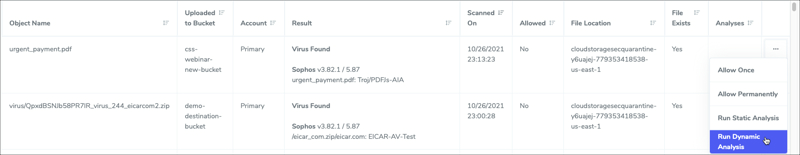
Figure 2. Selecting and running dynamic analysis (malware detonation) in the CSS console.
After the dynamic analysis has been completed, a report will be returned that contains information on the file itself, its commonality, IP addresses it’s attempting to connect to, and most importantly, the directories and processes the file tried to write to when executed. This can be found in the generated activity tree at the bottom of the report.

Figure 3. Example dynamic analysis report in CSS console.

Figure 4. Real activity tree generated by detonating a suspicious file.
In the example above, you can see that, if executed on a machine, this piece of malware is a trojan horse that would begin encrypting and exfiltrating files.
Getting Started
Implementing Cloud Storage Security alongside Amazon GuardDuty is an easy and effective way to ensure your entire cloud storage environment is protected against a growing onslaught of threats.
Implementing Amazon GuardDuty Malware Protection for Amazon S3
You can enable Amazon GuardDuty Malware Protection for Amazon S3 by signing into the AWS Management Console, opening the GuardDuty console at https://console.aws.amazon.com/guardduty/, navigating to the S3 Protection page on the left sidebar, and clicking “Enable Malware Protection for S3” within the “Protected buckets” table. From there, you can select which Amazon S3 buckets you’d like to enable protection for, select which prefixes, if any, you’d like to scan, and configure other functionality such as object tagging, granting GuardDuty the proper permissions, and malware protection policy IDs. After configuring all required settings and clicking “Enable”, GuardDuty will begin scanning objects that land in protected buckets and send any discovered malware to the "Findings" page in the GuardDuty console.
GuardDuty Malware Protection for S3 starts at $0.09/GB and $0.215/1k objects when the data resides in the us-east-1 region.
Implementing CSS Antivirus for Amazon S3
To get started with CSS, contact a SME today or subscribe to a fully-featured 30-day free trial in AWS Marketplace with the help or our Getting Started Guide—you'll be up and running in under 15 minutes.

%20(3)-1.png?quality=high&width=1900&height=1250&name=CSS%20-%20Blog%20(Featured%20Images)%20(3)-1.png)
%20(1).png?width=2000&height=1125&name=CSS%20-%20Blog%20(Featured%20Images)%20(1).png)



