
The Shared Responsibility Model for Object Storage
As malware attack vectors continue to grow and more and more security features are built above and below the delineation of “Security of the Cloud” (provided by AWS) and “Security in the Cloud” (your job), security teams will need to ensure a proper framework to protect their applications and data.
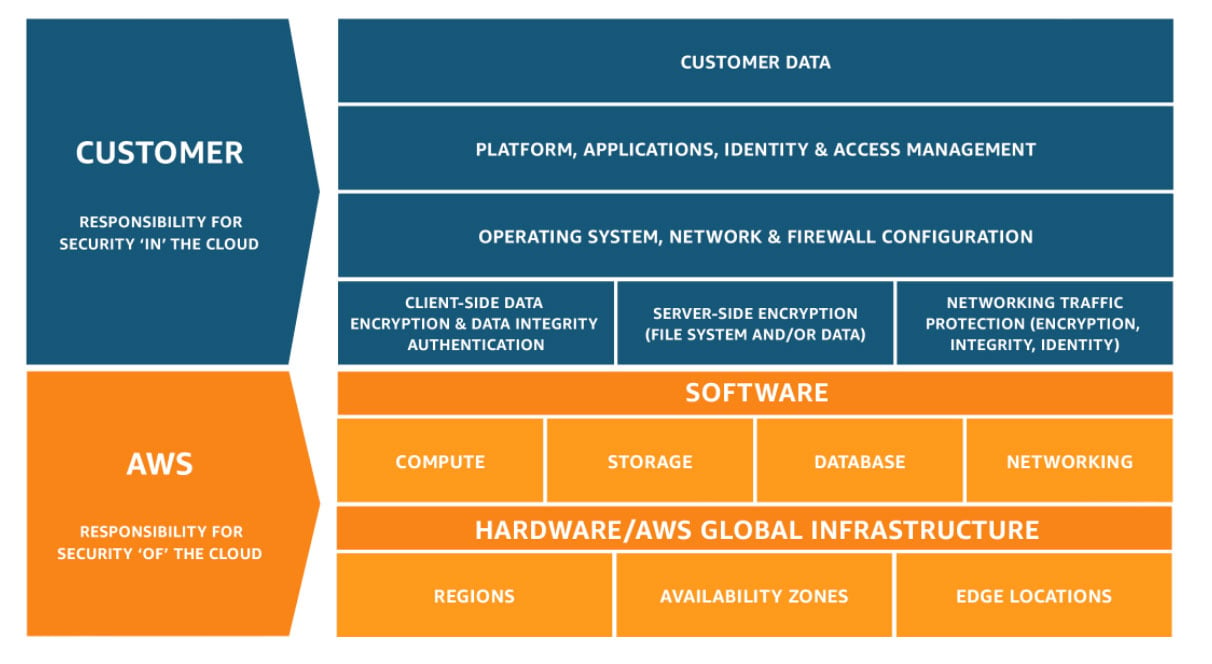
The Shared Responsibility Model helps identify the reduced operational burden for public Cloud customers, however, it is solely your role to protect all customer data and corporate data.
Here are some initial preventative practices to ensure your buckets, your data and your applications are safe. It is essential you ensure consistent cloud security controls and procedures across all account groups, users and roles. In addition, performing regular reviews of your written security framework will ensure the proper security controls and policy to keep your data and applications safe.
Ensure proper and correct Amazon S3 policies. Bucket permissions policy is set to private by default, however, only buckets that require public access to be exposed using Amazon S3 block public access. The Amazon S3 Block Public Access feature provides settings for access points, buckets, and accounts to help you manage public access to Amazon S3 resources.
Scan for malware and viruses. You should be scanning any buckets that are exposed to the public and specifically allow unknown third parties to write to your Amazon S3. In addition, outbound files should be scanned to ensure your customers and corporate applications are not at risk. It is your responsibility to keep your data lake free of malware. A free trial of Antivirus for Amazon S3 is available on the AWS Marketplace.
Least Privilege access. Only the minimal permissions should be granted to Amazon S3 resources using a multi-factor IAM.
Encryption is paramount. All data at rest and in transit should be encrypted. Encrypt, encrypt, encrypt. Get the point?
Enable Amazon S3 cross-region replication to extend your data across greater geographic zones.
Leverage AWS native tools like CloudTrail data events and CloudWatch alerting and logging.
Establish data lifecycle policies. It ensures data will ultimately age out and keep costs down.
Computer malware and viruses are rampant and an everyday fact of doing business. Historically malware has been delivered through email, web or even file sharing through network shares. The threat has evolved to include a new attack vector of uploading files to cloud storage. Users and applications have come to rely on public cloud to provide storage for critical business data. Cloud Storage Security Antivirus for Amazon S3 protects Amazon S3 storage.
Leveraging a consistent, written security framework will keep your object storage, files and applications safe from malicious intent and the hidden threats within Amazon S3.

%20(3)-1.png?quality=high&width=1900&height=1250&name=CSS%20-%20Blog%20(Featured%20Images)%20(3)-1.png)
%20(1).png?width=2000&height=1125&name=CSS%20-%20Blog%20(Featured%20Images)%20(1).png)


%20(7).png?width=387&height=258&name=CSS%20Webinar%20Thumbnails%20(750%20x%20750%20px)%20(7).png)
%20(1920%20x%201080%20px)%20(18).png?width=387&height=258&name=Copy%20of%20Blue%20White%20Gradient%20Modern%20Professional%20Business%20General%20LinkedIn%20Banner%20(750%20x%20750%20px)%20(1920%20x%201080%20px)%20(18).png)
