
Amazon Simple Storage Service (Amazon S3) launched close to two decades ago and houses over 200 trillion objects. Since launching over 15 years ago, Amazon Elastic Block Store (Amazon EBS) has transferred thousands of exabytes of data and delivered trillions of input/output operations; more than 390 million EBS volumes are created daily.
The popularity of using AWS storage services to run applications, scale data analytics workloads, backup and restore data, or archive data at low cost makes them attractive to federally regulated financial institutions (FRFI).
As storage is a primary data repository in cloud computing it should not be overlooked when complying with Office of the Superintendent of Financial Institutions of Canada (OSFI) Guideline B-13; the data can introduce cyber risk because it may contain malicious code or sensitive information.
As part of the AWS Shared Responsibility Model, FRFI’s are responsible for the security and compliance of their data. AWS does not scan data in storage by default, which leaves FRFIs and the customers they serve vulnerable if they are not addressing the risk of malware or sensitive data theft themselves.
This article introduces Guideline B-13 and discusses how Cloud Storage Security (CSS) helps customers automate and accelerate compliant workloads on AWS through malware detection, data loss prevention, and storage assessments.
Guideline B-13
FRFIs include Canadian banks as well as foreign bank and insurance branches, trust and loan companies, life insurance companies, property and casualty companies, cooperative credit associations, and fraternal benefit societies.1 FRFIs are supervised and regulated by OSFI, an independent agency of the Government of Canada.
OSFI’s Final Guideline B-13, effective January 1, 2024, establishes expectations for the management of technology and cyber risks across three domains, each of which have a specified desired outcome:
|
Domain |
1. Governance and Risk Management |
2. Technology Operations and Resilience |
3. Cyber Security |
|
Expectation |
Formal accountability, leadership, organizational structure and framework used to support risk management and oversight of technology and cyber security. |
Management and oversight of risks related to the design, implementation, management and recovery of technology assets and services. |
Management and oversight of cyber risk. |
|
Outcome |
Technology and cyber risks are governed through clear accountabilities and structures, and comprehensive strategies and frameworks. |
A technology environment that is stable, scalable and resilient. The environment is kept current and supported by robust and sustainable technology operating and recovery processes. |
A secure technology posture that maintains the confidentiality, integrity and availability of the FRFI’s technology assets. |
What’s more, OSFI released its final Integrity and Security Guideline on January 31, 2024, which establishes expectations for adequate policies and procedures to protect against threats. B-13 directly supports the Integrity and Security Guideline and FRFIs are required to submit to OSFI a comprehensive action plan that details how expectations will be met, including “interim deliverables to achieve compliance” by July 31, 2024.2
|
Key Compliance Dates
|
Defense in Depth
CSS provides data security for AWS storage services, which supports FRFIs in meeting OSFI B-13 expectations and in doing so also supports compliance with the new Integrity and Security Guideline.
To establish greater resilience against data breaches and operational disruption as well as financial and reputational loss, CSS helps FRFIs meet expectations pertaining to the following Technology Operations and Resilience and Cyber Security domains when it comes to data in cloud storage (OFSI B-13 defines data as an intangible “technology asset” that “needs protection and supports the provision of technology services”3):
- Inventorying data
- Managing configurations
- Reporting on data location by AWS account, region
- Proactively identifying security risks
- Identifying, classifying and protecting structured and unstructured data
- Implementing defense controls for data loss, malware and viruses
- Supporting access management controls
- Security logging
- User activity reporting
To see which Guideline B-13 expectations CSS helps FRFIs meet, refer to the CSS-OSFI Guideline B-13 Matrix.
FRFIs use CSS to baseline scan existing data on demand and on schedule as well as to scan new data in real time. When a scan completes, the results are generated and an alert is shared via Amazon Simple Notification Service (SNS).
Real-time result notifications are sent to the SIEM systems and tools the FRFI already has in place. If data is found to be infected or have sensitive information, it may be quarantined, tagged, deleted, or kept in place.
CSS reporting shows the scan outcome and type of data as well as where the data resides. Security attributes such as whether a bucket is publicly accessible or if the data is encrypted are also provided.
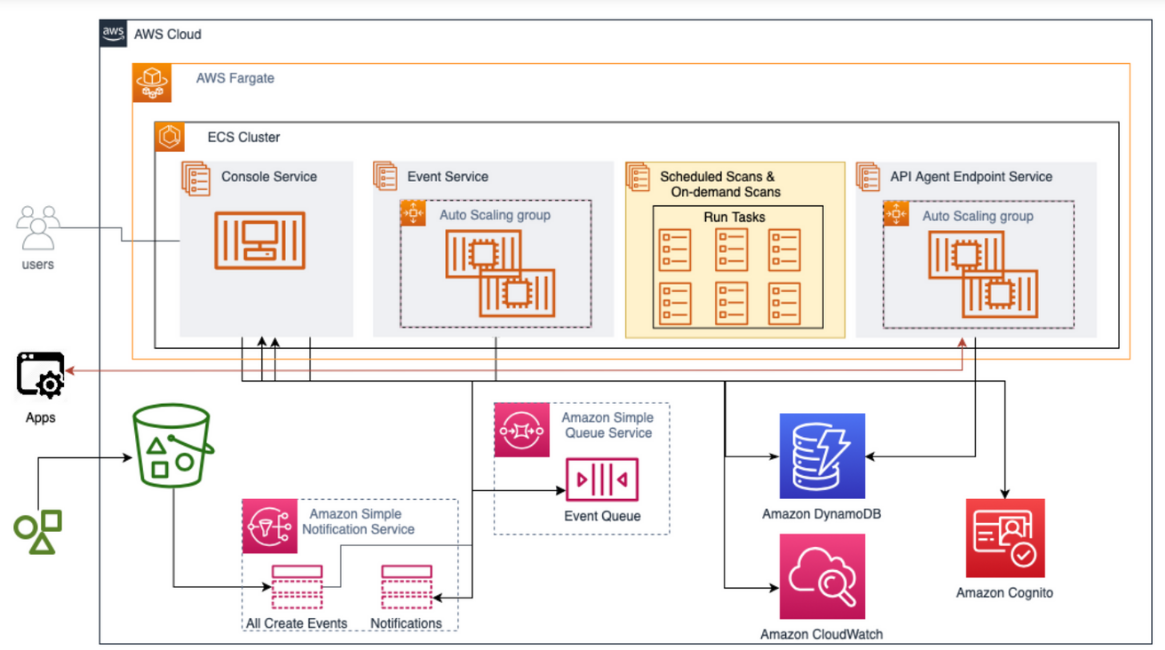
Figure: Cloud Storage Security Single Account & Region Architecture
Built for and powered by AWS, CSS inherits AWS controls and meets stringent private deployment requirements. Key product features include:
- Automated serverless security solution
- Runs in tenant; all data remains under the customer‘s sovereignty and control
- Real-time, on demand and scheduled scanning
- Antivirus engines include Sophos, CrowdStrike, and ClamAV
- Harnessed three decades of DLP experience
- Private VPC endpoint deployment option
About Cloud Storage Security
FRFIs turn to Cloud Storage Security (CSS) to meet compliance requirements and manage data security. Take advantage of a free trial in AWS Marketplace or contact CSS for more information including how to get started with a proof of concept (POC).
1https://www.osfi-bsif.gc.ca/en/supervision/who-we-regulate. 2https://www.osfi-bsif.gc.ca/en/guidance/guidance-library/integrity-security-letter. 3Final Guideline B-13. Per Guideline B-13, FRFIs are responsible for determining compliance requirements and validating control implementation in accordance with their company policies, requirements, and objectives. FRFIs should read Guideline B-13 in conjunction with other advice, including but not limited to the resources listed in section A.4 Related guidance and information of Final Guideline B-13.

%20(3)-1.png?quality=high&width=1900&height=1250&name=CSS%20-%20Blog%20(Featured%20Images)%20(3)-1.png)
%20(1).png?width=2000&height=1125&name=CSS%20-%20Blog%20(Featured%20Images)%20(1).png)




