
Cloud Storage Security (CSS) is always working to improve our users’ experience and we’re excited to share the following noteworthy Antivirus for Amazon S3 updates: Amazon EventBridge integration, AWS Control Tower integration, storage assessment, “suspicious” file identification, proxy enhancements, and read-only root files.
Amazon EventBridge
One of the most predominately used scan models within CSS' Antivirus for Amazon S3 (AVS3) solution is event scanning, which scans objects in near real time when they are dropped into Amazon S3. To do so, an event, in this case the All object create event, is leveraged on the bucket so any time an object is created/modified within the bucket an event is raised. AVS3 relies on Amazon Simple Queue Services (SQS) and AWS Lambda to listen for events in order to scan and process the data.
However, Lambda and SQS create a scenario in which the AVS3 scanning engine and the customer's existing workflow could not share events. To work around the issue required additional time and coding from the customer when deploying AVS3. Our integration with EventBridge bypasses these issues by allowing Lambdas, Queues, and AVS3 to each receive the All object create event and perform the work needed.
A new attribute, 'useEventBridge`, has been added to the Bucket→Protect API call to allow you to specify whether or not to use EventBridge with a given bucket. Typically, you'll want to use the EventBridge integration when using AVS3 event driven scanning. Reference CSS Help Docs for tips on EventBridge integration set up.
Additionally, if buckets reside in many accounts, EventBridge can be used as an alternative to S3 Events on any of those buckets. We released a new linked account role template to support EventBridge events across accounts; for now, you will need to manually upgrade the linked account role before EventBridge can be turned on for conflicted buckets in your linked accounts.
AWS Control Tower
CSS now supports Account Factory Customization - a newly released feature in AWS Control Tower. This functionality enables customers to:
- deploy the CSS console when provisioning new or managing existing accounts in AWS Control Tower
- streamline the account protection process by using linked accounts to automatically connect to the CSS console
Learn more in our announcement - CSS Supports AWS Control Tower to Enhance Data Security. Implementation steps can be found on the AWS Marketplace Blog in Automate Cloud Storage Security deployment using Account Factory Customization.
Storage Assessment
Designed to enhance data intelligence, our new Storage Assessment feature answer the questions: What do I have? Where is it located? What are my data trends? What coverage for scanning and encryption do I have for my storage?
Data points include, but are not limited to: total number of objects in Amazon S3, total number of objects encrypted, encrypted and unencrypted buckets by region, public and private bucket count.
This feature is automatically turned on when existing users upgrade to Console: v6.04.001, Agent: v6.04.000 through the standard console upgrade process; it can be disabled at upgrade by manually updating the stack and turning the drop down selection to False.
Storage Assessment crawls all of your data to provide an initial overview of all of the files you have stored in Amazon S3. After that initial crawl, Storage Assessment leverages S3 Inventory to continue to assess the data. Both the crawl and S3 Inventory have minimal charges associated with them.
Contact us to discuss Storage Assessment further.
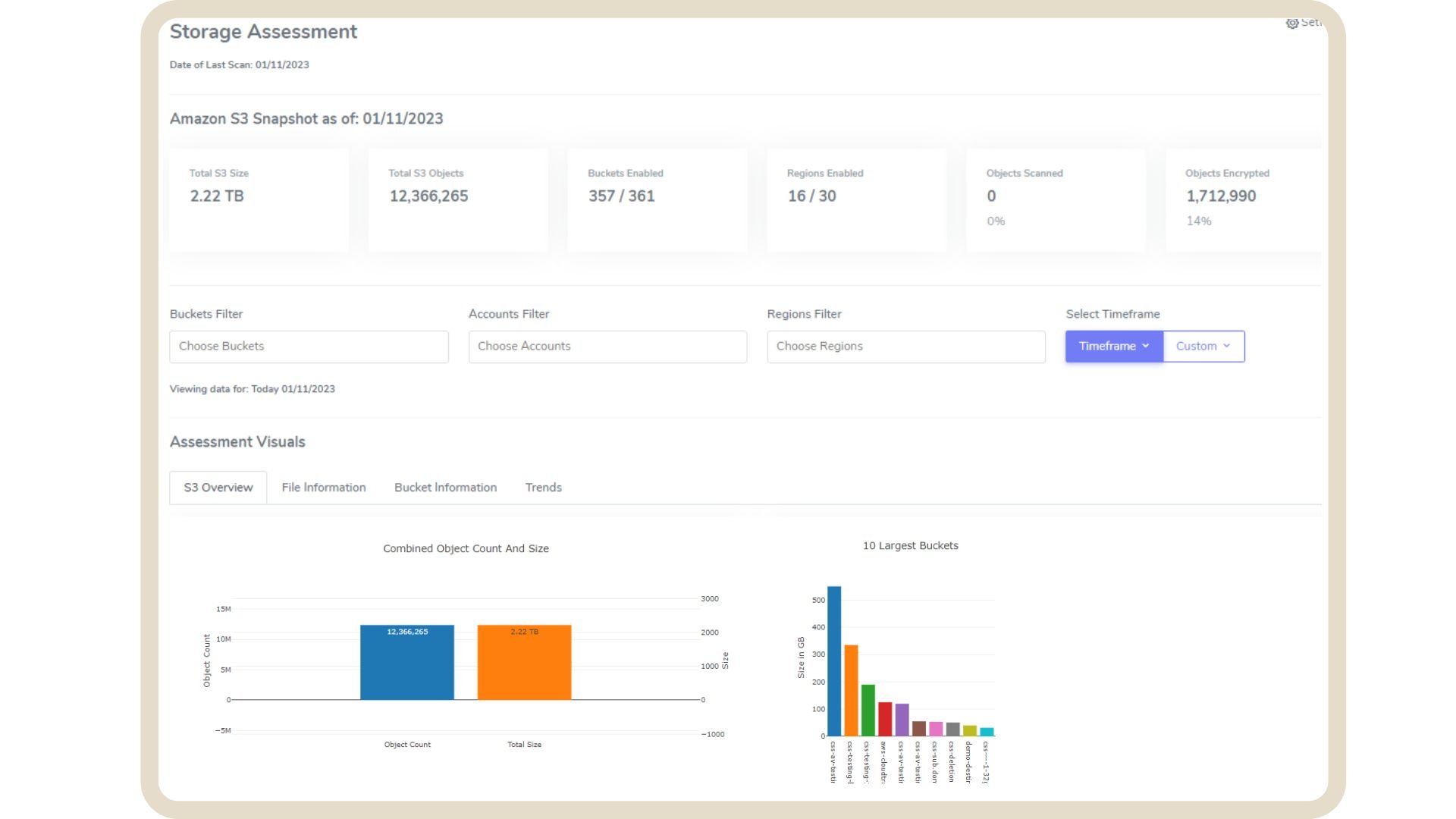
Storage Assessment Report in CSS Console
“Suspicious” File Identification
AVS3 offers multiple scan engines. Files that are scanned using signature-based detection that pass as Clean, could also be identified by the scan engine as files that warrant further investigation - perhaps through static analysis (compares data from other security vendors) or dynamic analysis (file detonation).
To tag files that should have a second look, we've added a new ScanResult attribute within the Sophos engine: scanResultKind.This attribute is filterable through Proactive Notifications.
Proxy Enhancements
To assist customers with creating more secure private deployments via proxy, we've made the following improvements:
- Extra Large File scanning via EC2 now supports proxy environments. Additional setup is required by adding two new VPC Endpoints: SSM and EBS; the plugin required to mount the large EBS volume is retrievable through a Public Amazon Elastic Container Registry.
-
Scanning agents now check for signature updates over proxy; previously, Private Mirror was required when deployed in
proxy mode. Note, the proxy must be open to allow for ClamAV traffic:.https://database.clamav.net
Read-Only Root Files
Our infrastructure is built around AWS Fargate containers in order to be serverless like AWS Lambda and faster and more flexible than Amazon EC2. To assist with compliance audit checks, Fargate container root file systems are now read-only.
Reference What's New for the latest release information and console, agent and CloudFormation template versions on in the CSS Help Docs.

%20(3)-1.png?quality=high&width=1900&height=1250&name=CSS%20-%20Blog%20(Featured%20Images)%20(3)-1.png)
%20(1).png?width=2000&height=1125&name=CSS%20-%20Blog%20(Featured%20Images)%20(1).png)



